Bus Topology
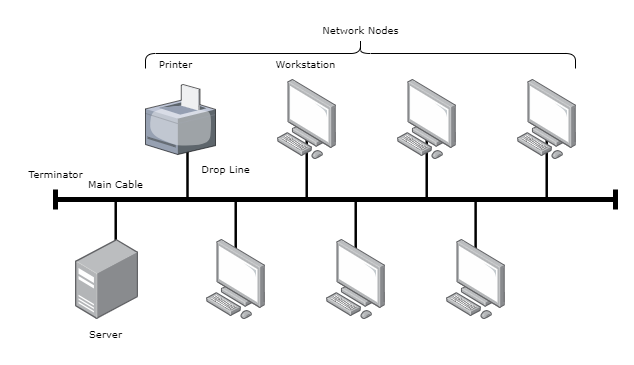
This setup connects all devices (Network Nodes) in a sequence on a single cable or ‘bus’. Data travels back and forth along the bus, and devices listen for data meant for them.
Components:
- Main Cable (Bus) – Central backbone of the network, to which all the network nodes are connected. Typically, this is a single coaxial cable or an RJ45-based Ethernet cable that runs throughout the network
- Terminators – Placed at the both ends of the main cable. These are used to prevent signal reflection at the ends of the cable, which can cause the data to bounce back and forth and result in interference or data corruption.
- T-Connectors – Used in networks where coaxial cable is the medium, these allow multiple devices to connect to the bus without any disruption to the main cable.
- Network Interface Cards (NICs) – Each network node is equipped with a NIC that allows it to connect to the main bus cable, these interpret data and electrical signals to and from the network to handle communication over the cable.
- Drop Line – Connection line from the network node to the main cable, typically short, these are used to minimize the distance between the device and the main cable, reducing the possibility of signal degradation.
- Network Devices (Nodes) – These are the computers, printers, servers, routers, switches connected.
Advantages
- Requires less cable than other topologies.
- Simple to implement in small networks.
- Reduced Costs.
Disadvantages
- Limited number of devices connected before the signal degrades.
- If two devices transmit at the same time, collisions occur, which can reduce efficiency.
- A problem with the main cable can bring down the entire network.
Use Scenarios:
- Small Branch Offices: Suitable for small networks or branch offices with a limited number of endpoints, where network traffic is minimal and cost is a critical factor.
- Temporary Networks: Good for quick, temporary setups, such as for workshops or event management, due to easy setup and minimal cabling.
Limitations
- The performance of bus topology degrades as more devices are added. There is a physical and practical limit to the number of devices that can be attached without significant loss of efficiency and performance.
- If the main cable fails, the entire network goes down. This single point of failure makes it less ideal for environments where network reliability is crucial.
- Since all communications happen over the same cable, data collisions are more frequent, especially as network traffic increases. This is managed by collision detection mechanisms like CSMA/CD (Carrier Sense Multiple Access with Collision Detection), which can prevent data packets from interfering with each other but at the cost of network performance.
Star Topology
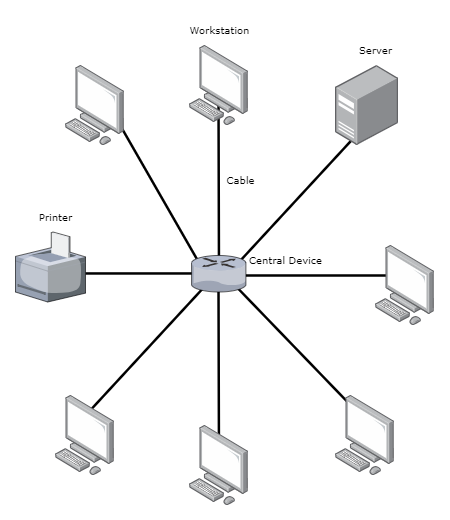
In this setup each device connects directly to a central device, like a hub or switch, that manages the network traffic. This topology is common because if one link fails it doesn’t affect the others.
Components:
- Central Device – Hub or Switch, these central devices are crucial in star topology as they serve as the point of connection for all devices.
- Cables – Each device is connected o the central device using a cable. This could be a coaxial cable, twisted-pair cable, or fiber optic cable, depending on network requirements for speed and bandwidth.
- Network Interface Cards (NICs) – Each network node is equipped with a NIC that facilitates communication over the network, it prepares, sends, and controls data on the network.
- Network Devices (Nodes) – These are the computers, printers, servers, routers, switches connected.
Advantages
- Adding or removing devices only affects the connections to the central device and not the rest of the network.
- Each device is connected independently to the hub, so problems in one cable won’t affect others.
- Faulty parts can be easily identified and replaced.
Disadvantages
- The entire network depends on the central device, if it fails the whole network goes down.
- More expensive than Bus due to the cost of hubs.
Use Scenarios:
- Office Buildings: Ideal for modern office environments where systems can be connected to a central device (hub, switch), giving better management and maintenance.
- Home Networks: Common in home WiFi networks where several devices are connected to a single hub.
Limitations
- The entire network depends on the functioning of the central hub or switch, if it fails the whole network is impacted.
- This topology might involve higher costs due to the need for more cable and the cost of hubs or switches.
Ring Topology
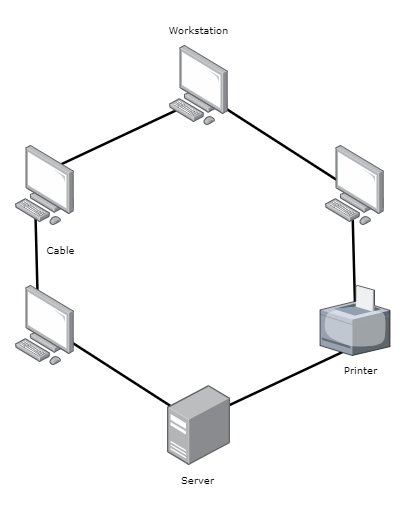
Devices are connected in a closed loop or ring, data passes in one direction from one device to the next and circulates around the ring until it reaches its destination, each device has exactly two neighbours for communication purposes.
Components:
- Network Interface Cards (NICs) – Each network node is equipped with two NICs to handle communication over the network, in a ring topology these are particularly configured to pass data packets along to the next device in the ring until the packets reach their destination.
- Cables – The connection between devices is made using cables, these can be coaxial, twisted-pair, or fiber optic cables. Each device is connected to its immediate Neighbours by separate cables, forming a closed loop.
- Repeaters (Optional) – In larger rings, or where data needs to travel long distances between devices, these might be used to regenerate the signal and prevent data loss, ensuring that signals remain strong enough to complete the circuit around the ring without degradation.
- Multistation Access Unit (MAU) – In some ring networks, particularly those using Token Ring technology, a MAU is used. It acts similarly to a hub or switch in star topologies but maintains the ring structure logically even if physically it looks like a star. These facilitate the management of the network and can automatically reconfigure the ring in case of node failure, maintaining the network’s operational status.
- Network Devices (Nodes) – These are the computers, printers, servers, routers, switches connected.
Advantages
- Data travels in one direction, reducing the chances of packet collision.
- Each device has equal access to resources and the network
Disadvantages
- A problem in any one of the devices can impact the entire network.
- Adding or removing devices can disrupt the operation of the network.
Use Scenarios:
- Real-Time Applications: Effective in real-time operations such as those found in control systems for trains or metros, where each station can retransmit the data to the next.
- School Networks or Small Offices: Where reliability is important and can be managed with the simplicity of having each device connected to two others.
Limitations
- If any single connection in the ring breaks, the entire network can be disrupted. This can be mitigated by implementing a dual ring or using switches that can reroute traffic.
- Adding or removing devices can disrupt the network unless systems are designed to handle such changes dynamically, as with the MAU in Token Ring networks.
Mesh Topology
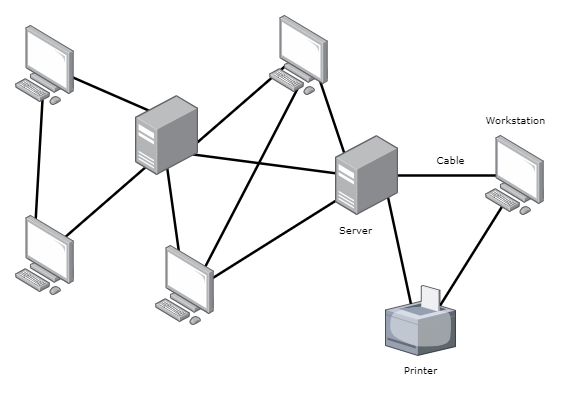
Every device connects directly to every other device in the network. This topology provides multiple pathways for data between any two devices, enhancing redundancy and reliability.
Components:
- Network Devices (Nodes) – These are the computers, routers, switches, and other communication devices.
- Network Interface Cards (NICs) – Each device is equipped with (𝑛−1) NICs, where 𝑛 is the total number of devices in the network. These manage the communication over multiple network connections, and in mesh topology these must handle more complex tasks due to multople active connections per node.
- Cables (Physical Mesh) or Wireless Links (Wireless Mesh)
- Physical mesh networks use various types of cables optical fiber, ethernet to connect nodes directly.
- Wireless mesh networks use radio frequencies or infrared signals for connections between nodes, eliminating the need for physical cabling.
- Routing and configuration software – Mesh networks often use sophisticated routing protocols like OSPF (Open Shortes Path First) or BGP (Border Gateway Protocol), these are essential for managing the routing of data across multiple paths. Software must dynamically adjust routes based on network availability and link integrity.
- Routers and switches (Larger Mesh Networks) – Routers and switches can manage data flow and ensure that data packets find the fastest and most reliable paths. Routers in a mesh network often need to support complex network topologies and handle a high volume of data transfer.
Types:
- Full Mesh Topology
- Every node is connected to every other node.
- Provides the highest level of redundancy.
- Typically used in smaller networks due to high number of connections required.
- Partial Mesh Topology
- Not all nodes are directly connected to every other node.
- Some nodes are connected to all others, while others are connected to a few.
- More scalable than full mesh and still provides good redundancy.
Advantages
- Failure of one device does not necessarily disrupt the network.
- Multiple paths for data to travel, so it’s highly reliable and fault-tolerant.
- Multiple active paths can balance the load.
Disadvantages
- More expensive due to the cost of redundant connections.
- Management and setup are challenging due to the complexity of connectivity.
Use scenarios:
- Data Center Networking: Ideal for environments requiring high availability and redundancy, such as in data centers where multiple pathways mitigate the risk of connectivity loss.
- Military communications: Used in military bases or operations where maintaining network integrity and availability under all conditions is crucial.
Limitations
- The complexity of managing a mesh network increases with the number of interconnections. Each new node added to the network significantly increases the number of required links.
- Maintaining this type of network requires continuous monitoring and updating to ensure all nodes are functioning properly and efficiently.
Tree Topology
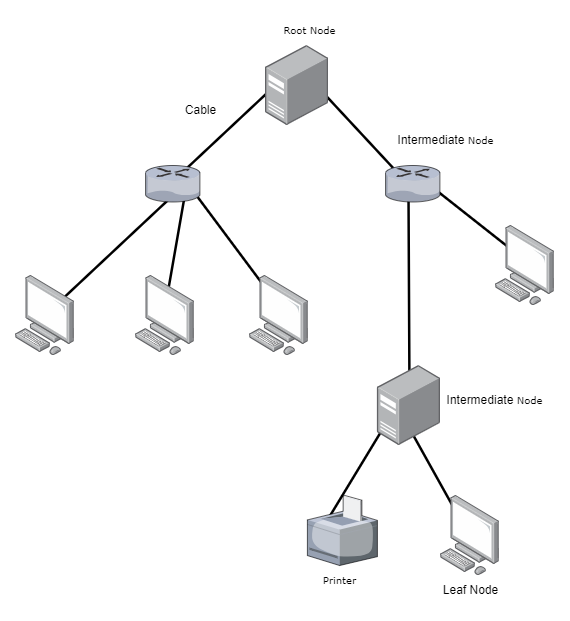
This is a variation of the star topology but with multiple levels. You can think of it as stars interconnected by more stars. It’s hierarchical, so all data destined for the network passes through the top level and goes down to the lower levels.
Components:
- Root Node – This is the top-level node and acts as the central hub of the tree topology, it controls the network and serves as the gateway for all the network traffic. This connects directly to one or more intermediary nodes, forming the backbone of the network.
- Intermediate Nodes – These are the second-level nodes and can be thought of as hubs or switches that control the traffic to and from the leaf nodes. These expand the reach of the network by branching out from the root node, facilitating communication between the leaf nodes and the rest of the network.
- Leaf Nodes – These nodes represent the end user devices such as computers, printers. Leaf nodes don’t communicate directly to each other but communicate through their connecting intermediate nodes or directly to the root node.
- Cables – Various types of cables can be used depending on the network’s scale and bandwidth requirements, including coaxial cables, fiber-optic cables, or twisted-pair cables. Each node is connected through these cables, which carry data across the network.
- Network Interface Cards (NICs) – Each node is equipped with a NIC that facilitates communication over the network these are crucial for converting data into a format suitable for transmission and managing traffic between computers.
Advantages
- Easy to expand, especially useful for networks that plan to expand.
- Easy to identify and isolate faults.
Disadvantages
- The entire network depends on the health of the central device, if it fails the entire network fail.
- More difficult to configure and wire than other topologies.
Use Scenarios
- Large Corporate Networks: Suitable for large enterprises with many departments, allowing them to organize the network in a hierarchy that mirrors the organization.
- University Campuses: Useful in academic campuses where different buildings may need individual networks that still connect to a central backbone.
Limitations
- If the main root node or any intermediate node fails, entire segments of the network can become isolated and non-functional creating points of failure in the network.
- As the network grows, the complexity of cables and configuration increases. This can make setup and maintenance cumbersome and costly, especially in very large networks.
Hybrid Topology

This combines two or more different topologies within the same network.
Components
- Different topology structures
- Star: Often used as central hub for connecting other topologies because of its robustness and ease of managing connections.
- Ring: Can be integrated to provide dedicated pathways for data to circulate, enhancing fault tolerance and performance.
- Bus: Use for cost-effectively connecting different groups or departments within a larger network.
- Mesh: Provides high redundancy and reliability, especially useful in critical network segments where data loss cannot be tolerated.
- Routers and Switches – Routers are used to connect different network segments and direct data packets between them. Switches are employed within specific topology segments (like star or mesh segments) to manage traffic efficiently within those networks.
- Bridge – Bridges are used to connect different network segments that may operate under different protocols. They filter traffic and reduce collisions by dividing traffic into segments.
- Gateway – These facilitate communication between networks that use different protocols. They are crucial in hybrid topologies for ensuring seamless data flow across diverse network architectures.
- Cables and Wireless Links – The choice of cabling or wireless depends on the specific topologies integrated within the hybrid network. Coaxial cables, giber optics, or Ethernet cables might be used alongside wireless radio frequencies or infrared.
- Network Interface Cards (NICs) – Each device in the network needs a NIC that is compatible wit the network’s standards and protocols, capable of handling the specific requirements of the hybrid technology.
Advantages
- Combines the strengths of two or more topologies.
- Can be expanded easily without disrupting existing architecture.
Disadvantages
- Can be more complicated to design and maintain.
- More expensive than implementing one single topology due to the complexity and hardware required.
Use Scenarios:
- Enterprise Networks: Best for large-scale businesses that require the flexibility of combining various topologies to meet different departmental needs while ensuring overall connectivity and security.
- Growing Businesses: Suitable for organizations that anticipate future network expansion or changes, allowing them to integrate various topologies as needed without major overhauls.
Limitations
- Managing a hybrid network can be challenging due to the integration of different topologies and technologies. This complexity requires skilled network administrators and sophisticated network management tools.
- While the network design might be cost-effective, the operational costs can be higher. Troubleshooting and maintenance in such a complex network can require more time and resources.
Challenge: Identify each different Topology on the Hybrid Topology image, and answer in the comments.





















