The Pyramid of Pain is a concept in cybersecurity that helps to visualize and understand the impact of various indicators of compromise (IOCs) on adversaries, illustrating the increasing levels of difficulty an attacker faces when their activities are detected and blocked by defenders.
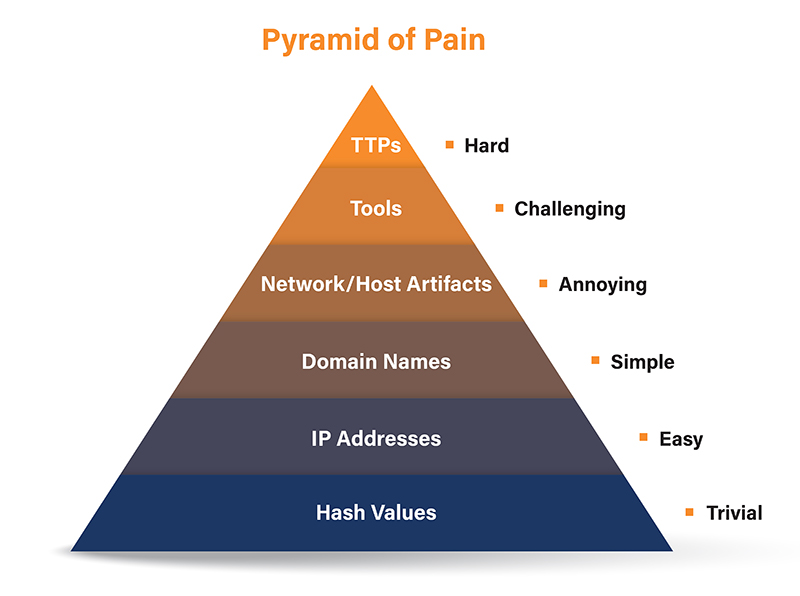
- Hash Values
It has a easy difficulty for adversaries as they can easily change hash values by altering even a single byte in the file.
- IP Addresses
It has a low difficulty for adversaries as they can quickly change IP addresses using dynamic DNS, VPNs, or other methods.
- Domain Names
It has a low to moderate difficulty for adversaries as changing domain names is relatively easy but requires more effort than changing IP addresses.
- Network/Host artifacts
It has a moderate difficulty for adversaries as altering these requires changes in the malware or the attack method. Artifacts include specific network patterns or host-based indicators like file paths or registry keys.
- Tools
It has a challenging difficulty for adversaries as creating or obtaining new tools is more challenging and resource-intensive.
- Tactics, Techniques, and Procedures
It has a very challenging difficulty as changing TTPs to achieve their goals requires significant changes in the attack methodology and may involve training new operators.
Defenders will have more impact by blocking the more challenging IOCs for adversaries to change.





















