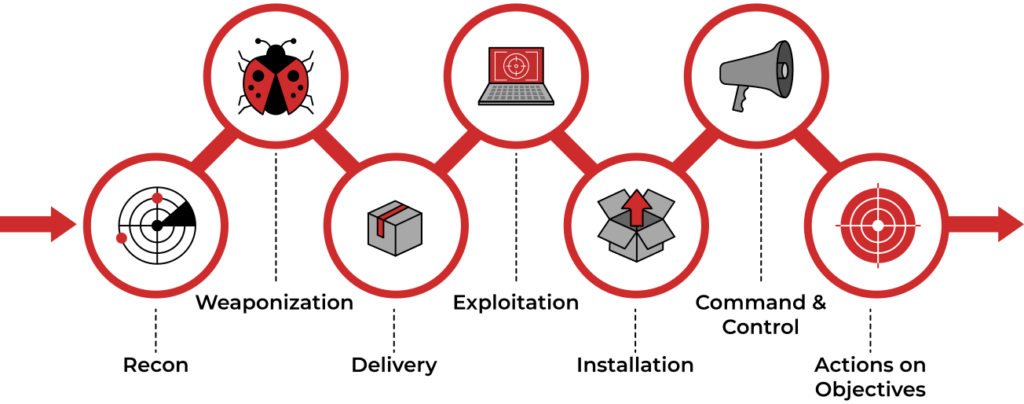
The Cyber Kill Chain is a framework developed by Lockheed Martin to describe the stages of a cyber attack, understanding it helps organizations identify and prevent cyber attacks by breaking down the attack into manageable phases.
- Reconnaissance
In the reconnaissance phase the objective is gathering information about the target by researching, identifying, and selecting targets using various tools and techniques like web searches, social engineering, and network scanning.
- Weaponization
In this phase the attacker will create a deliverable payload/malware or an exploit to a vulnerability to be used against an identified target.
- Delivery
This stage consists in delivering the payload/malware created on the previous stage via email attachments, USB drives, websites, exploitation of a vulnerability, or other methods.
- Exploitation
The exploitation phase consists in exploiting a vulnerability previously discovered with success and execute code on the target system, in this phase cybercriminals often move laterally across a network to reach their targets.
- Installation
After cybercriminals exploit the target’s vulnerabilities to gain access to a network, they begin the installation stage where they attempt to install malware and other weapons onto the target network to take control, maintain persistency and exfiltrate data.
- Command and Control (C2)
In this stage cybercriminals communicate with the malware they’ve installed onto the target’s network to instruct them to carry their objectives and enable remote control of the infected systems.
- Actions on Objectives
In the actions on objectives phase attacker’s perform actions to achieve the attack objectives like weaponizing a botnet, distributing malware to steal sensitive data, and using ransomware.





















